SSO Configuration
Audience
Audience: Administrators
Overview
Single-Sign-On (SS0) applications enable users to access all of their enterprise systems in one place. OrgChart supports SAML 2.0 Single Sign-On, which makes it compatible with most Identity Management Systems.
Administrators can integrate OrgChart with their Identity Management System directly in the OrgChart application.
This article covers the following topics:
Additional SSO Configuration Settings
SAML attributes handling
Auto-provisioning users
Single Logout
OrgChart Metadata
OrgChart metadata is unique to each customer. To find your OrgChart metadata, follow these steps:
Log in to OrgChart.
Click on the Mode Switcher icon in the Top Toolbar, and then select the Setup option. The Setup panel is displayed.
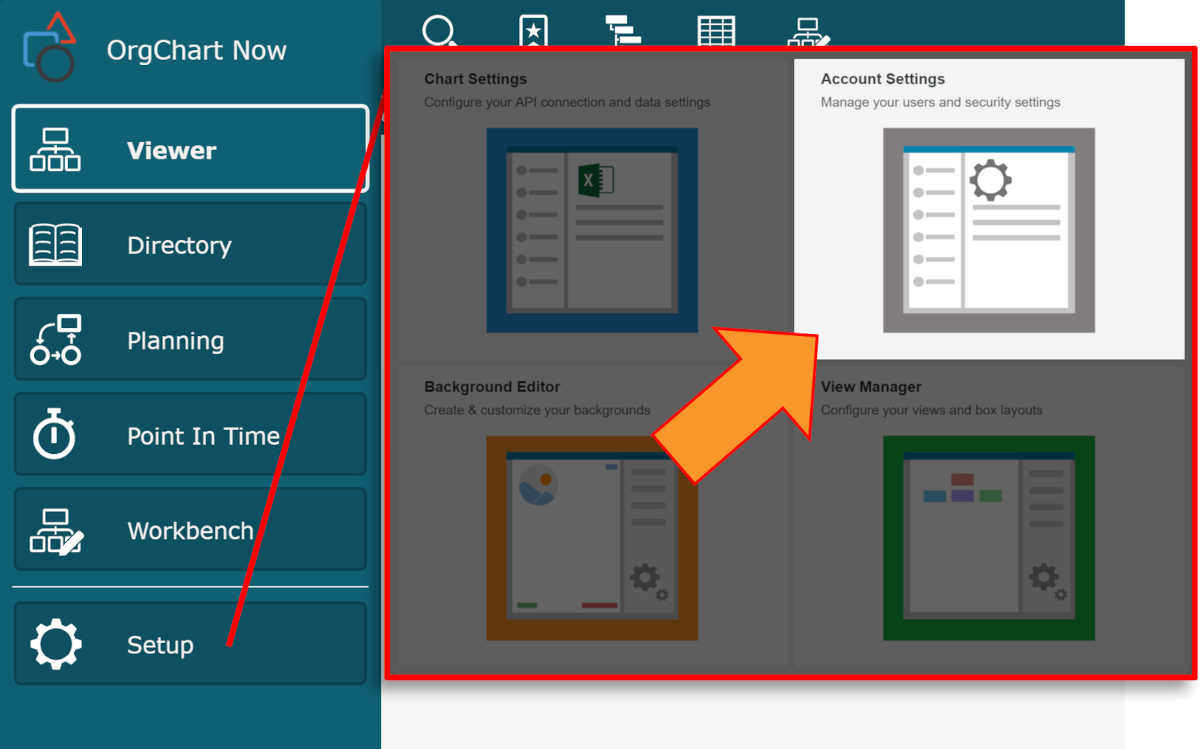
Click on the Account Settings tile, and then click on the Authorization tab in the left side menu.
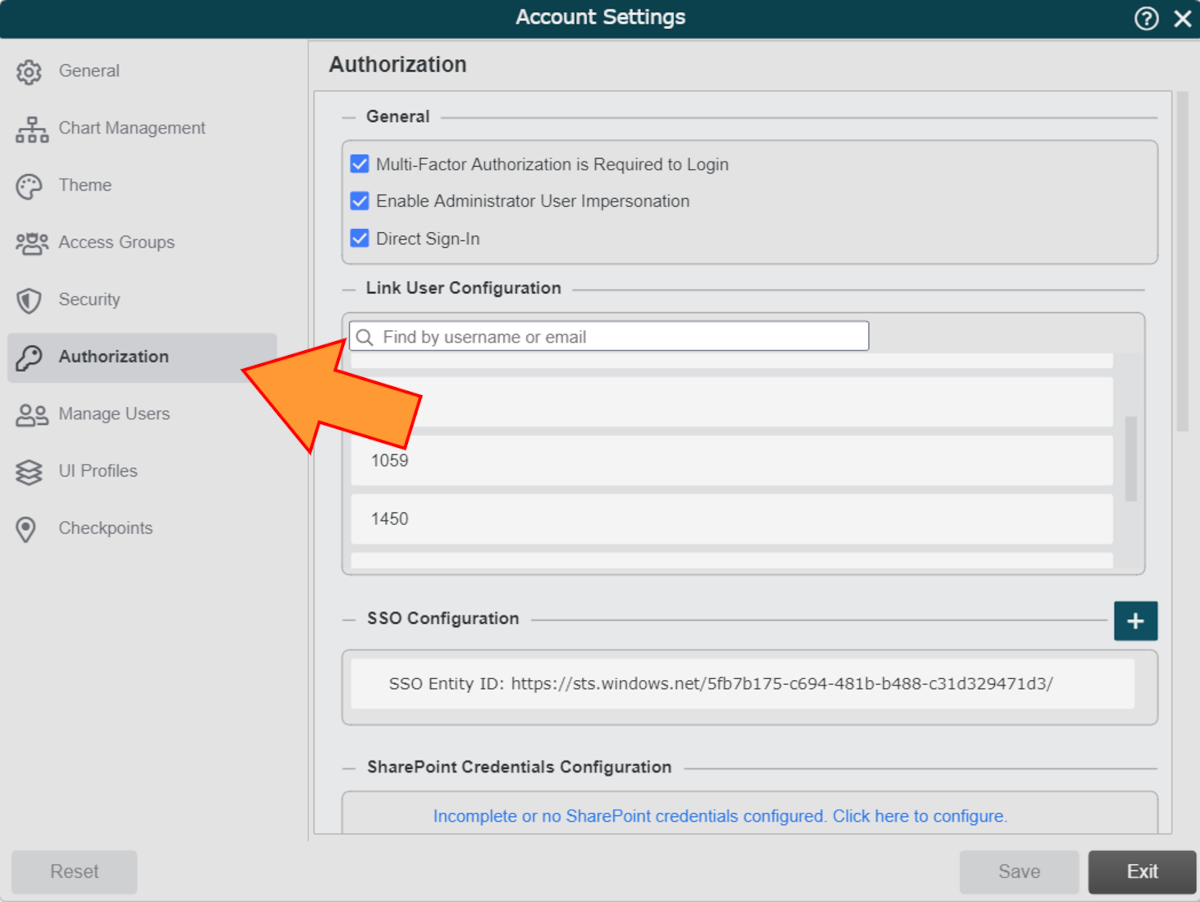
Click on the
 icon (to the right of the SSO Configuration heading). The SSO Configuration panel is displayed.
icon (to the right of the SSO Configuration heading). The SSO Configuration panel is displayed.Ensure that you have entered your IDP Entity ID into the SSO Entity ID text box.
Note
This is the Entity ID that is associated with your Identity Provider (i.e. Okta). For more information on how to obtain your IDP Entity ID, contact your IDP System Administrator, or reference one of our SSO integration guides:
Scroll to the bottom of the SSO Configuration panel, and then click on the SAML SP Metadata button.
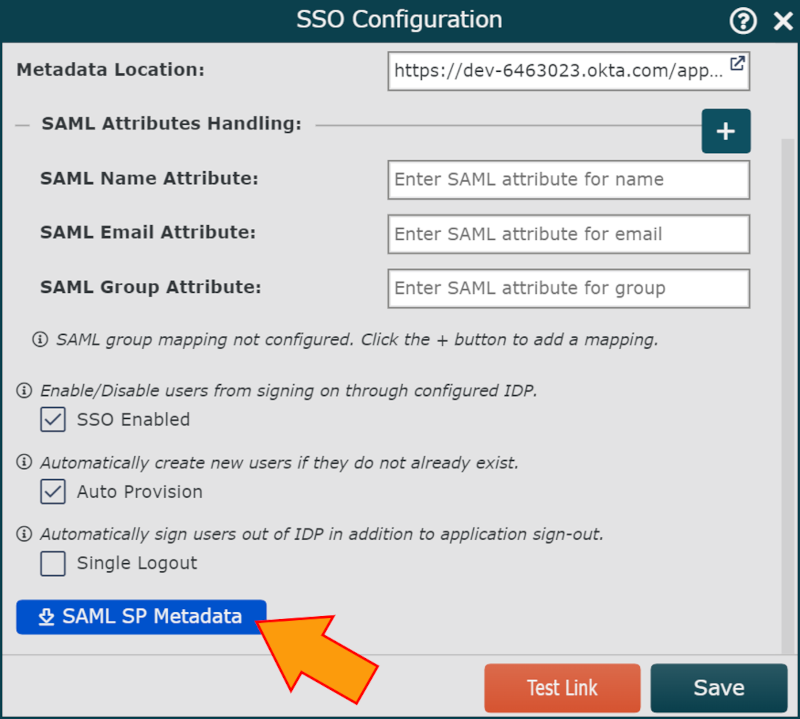
An XML file of the metadata associated with your account is downloaded. When opened, the file will look similar to this:
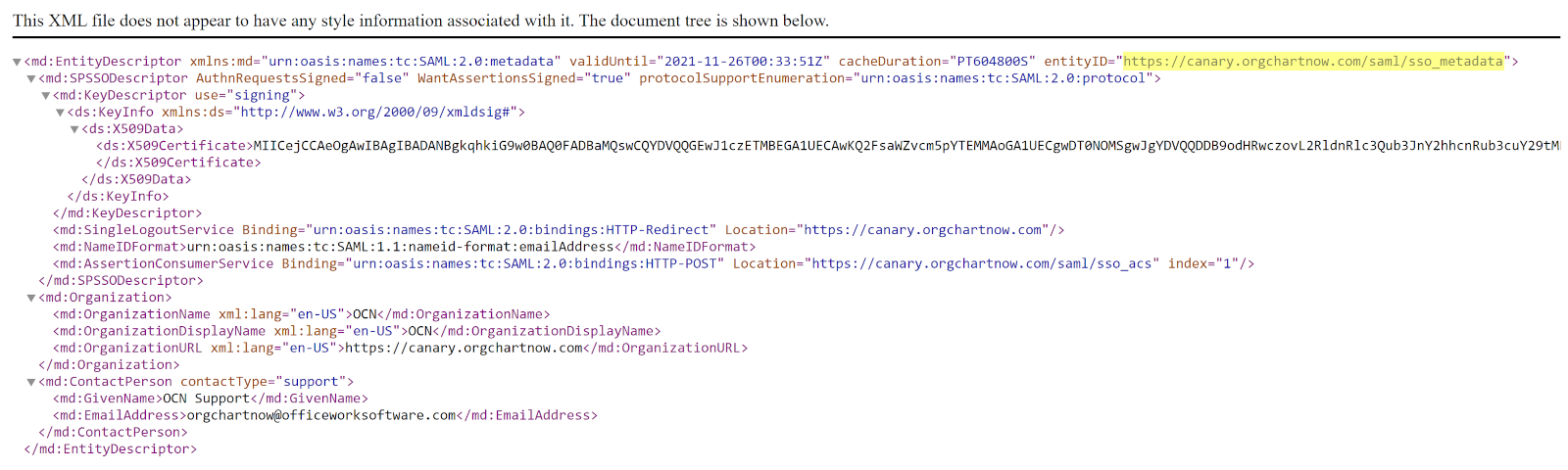
Note
OrgChart's entityID is highlighted in the screenshot above. This value is often needed when configuring SAML in your IDP, and can be referred to in the following terms:
Identifier (Entity ID)
Service Provider Entity ID
Audience Restriction URL
Audience URL
IDP SAML Configuration
Within your IDP, you will have to configure your SAML options according to the schema provided below.
Single Sign on URL: https://{SERVER NAME}.orgchartnow.com/saml/sso_acs?entityID=YOURENTITYID
Recipient URL: https://{SERVER NAME}.orgchartnow.com/saml/sso_acs?entityID=YOURENTITYID
Destination URL: https://{SERVER NAME}.orgchartnow.com/saml/sso_acs?entityID=YOURENTITYID
Audience Restriction: https://{SERVER NAME}.orgchartnow.com/saml/sso_metadata?entityID=YOURENTITYID
Name ID Format: Email Address
Note
YOURENTITYID is the entity ID in your IDP-generated metadata.
Important
Not all IDPs use the same vocabulary, and some IDPs require additional internal setup. Please reference one of the use cases below to ensure that your IDP SAML configuration is correct:
Configuring SSO
Log in to OrgChart.
Click on the Mode Switcher icon in the Top Toolbar, and then select the Setup option. The Setup panel is displayed.

Click on the Account Settings tile, and then click on the Authorization tab in the left side menu.
Click on the
 icon (to the right of the SSO Configuration heading). The SSO Configuration panel is displayed.
icon (to the right of the SSO Configuration heading). The SSO Configuration panel is displayed.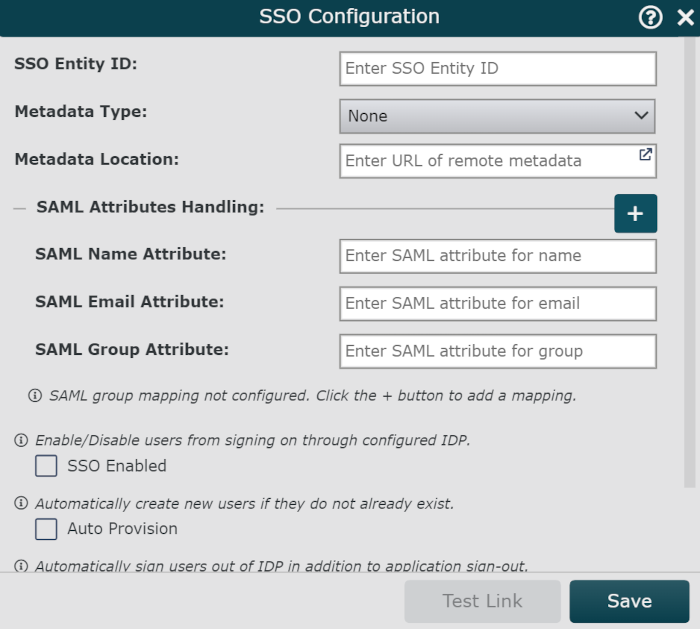
Enter the SSO Entity ID associated with your IDP (Identity Provider).
Select the metadata type in the Metadata Type dropdown menu. Metadata types include:
Remote - Metadata can be accessed using a URL.
Local - Metadata is not publicly accessible and must be uploaded as an XML file.
Note
If you are updating local metadata, ensure that your file name DOES NOT INCLUDE symbols (i.e. dashes, ampersands, etc.)
Enter the URL associated with your remote metadata, or drag and drop your Local metadata into the SSO Configuration panel to upload it to OrgChart.
Check the SSO Enabled checkbox to enable users to sign in to OrgChart through the IDP.
Optionally, check the Auto Provision checkbox to create new users in OrgChart (if they do not already exist) when first accessing the application from the IDP.
Optionally, check the Single Logout checkbox to enable SLO. When SLO is enabled, users who sign out of OrgChart will automatically be signed out of their IDP.
Click Save.
Additional SSO Configuration Options
The following options are available in the SSO Configuration panel, but are not required for a fully functioning SSO integration:
SAML Attributes Handling | Automatically update user information and/or assign OrgChart Access Groups to users based on their IDP security group. Reference the SAML Attributes Handling section below for more information. |
Auto-Provision | Check to automatically create a user in OrgChart (if one does not already exist) upon a user's initial sign-on via SSO. |
Single Logout | Check to automatically sign users out of their IDP when they sign out of OrgChart. |
The following option is available in the Account Settings: Authorization panel:
Direct Sign-In | Uncheck to disable users from logging in to the application via the OrgChart landing page. Users who attempt login will automatically be forced through the SP initiated SSO process, and redirected to their IDP for authentication. NoteEnabling or disabling Direct Sign-In is applied account-wide. |
SAML Attributes Handling
OrgChart can interpret certain SAML attributes for the following uses:
Populate the UserID field in the Account Settings: Manage Users panel using the SAML Name Attribute.
Populate the Email field in the Account Settings: Manage Users panel using the SAML Email Attribute.
Map security groups from your IDP to the appropriate OrgChart Access Group using the SAML Group Attribute .
Note
OrgChart also allows you to map IDP security groups to any of the three options:
Full Access + Admin Role
Full Access + Read/Write Role
Full Access + Read Only Role
Full Access, unlike user-created Access Groups, allow the assigned user access to all Master Charts and Views within the account. The associated role dictates how the user can interact with Master Charts, Views, and Account Settings.
For more information on configuring SAML Attributes Mapping, reference one of the IDP specific articles below:
Note
When SAML Attribute Mapping is configured, OrgChart will always respect the information provided by the IDP. For example, if your security assignment changes in your IDP, your OrgChart Access Group will be updated upon next login.
Important
IDP Security Group mapping cannot be overridden using the Bypass Data Driven Group Assignment feature in the Account Settings: Manage Users panel.
Verifying Your SSO Configuration
You can test your SSO configuration by attempting SP-Initiated SSO. Use the formatting below to create a URL that you can copy into your web browser:
https://{SERVER NAME}.orgchartnow.com/saml/sso_endpoint?entityID=YOURENTITYID
Note
YOURENTITYID is the entity ID in your IDP-generated metadata.